There are 4 stages to implementing a security solution:
- Risk analysis and definition of requirements
- Concept proposal
- Choice of services and technologies
- The "as a service" business proposition
1. Risk analysis and definition of requirements
We always offer to carry out a Security Scan using our Security Solutions Tool (SST).
Objective: to support clients with identifying and prioritising risks so we can offer them appropriate solutions to reduce their exposure.
The plus point: it's a great opportunity to exchange ideas and get a real feel for what's going on in the field.
The methodology factors in:
- Identifying the risk and how it may occur
- Risk analysis based on the probability of occurrence and its severity
- Identifying and studying vulnerabilities
- Assessing the risk level and prioritising treatment
2. Concept proposal
As a follow-up to the SST, we are working on a concept to make video coverage and/or the anti-intrusion system more visual.
It's always a question of strategically positioning the equipment to give operators the resources they need to carry out effective video surveillance. These may be detectors such as radar or thermal cameras, or fixed or mobile optical cameras. Loudspeakers enable the central monitoring station operator to take control remotely and to challenge intruders if necessary.
Of course, we can connect existing equipment.
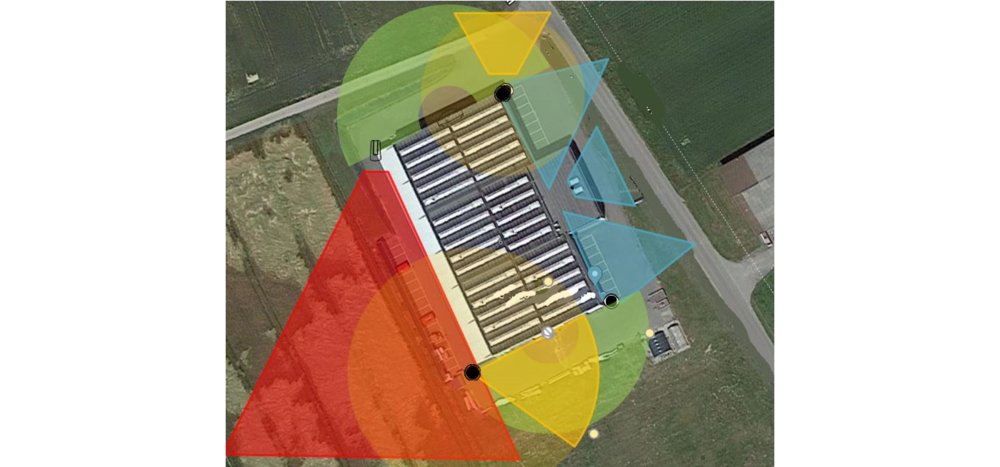
Example of a security plan
- The scope of the thermal camera is displayed in red, and the radar is displayed in green -> this shows the perimeter detection zone.
- Yellow is used for the mobile camera, which automatically tracks any movement detected and helps to eliminate any doubt
- Blue is used for the fixed cameras at access points, also providing motion detection via analytics.
3. Choice of services and technologies
Depending on the site's specific needs, we work with the customer to decide on the most appropriate combination of services and technology:
- Technology
- On-site or mobile security guards (intervention)
- Connection to the SOC for remote services (e.g. alarm detection, remote opening, etc.)
4. The "as a service" business proposition
Once we have agreed on the concept and services with the customer, we produce a business proposal:
- over a contract period generally varying from 24 to 60 months,
- including the provision and maintenance of the technology (no investment in equipment required),
- the services,
- and guarding (security guards on site, on rounds, or on call-out)
This is what we call a security solution.

About Protectas Security Solutions
Our Security Solutions are customised security packages that combine technology with a range of physical security services for both security and efficiency (cost optimisation and control). By providing them with the right combination of technology-based solutions, we relieve our customers of the burden of security, allowing them to concentrate fully on their core business.
* = mandatory fields

